6b7835db, 80a69d0f, de8ba884
these password are not working, Is every device has different password, can you share step to get password
6b7835db was what worked for me. To get the password I opened it up and dumped the NAND flash. Searched the dump for root: to find the shadow file. In there you have a hashed password - found two of these. Used hashcat with filters to look for a matching password (lower case letters and numbers length 8).
Will continue poking round see if theres an easier way to get root terminal.
Is it a special way to use it with local Tuya?
It will be shown as unsupported.
Or do I use the wrong integration ![]()
Tuya Local has it integrated, you might be using the wrong one, this is the one I use:
Okay thanks… Ive tried to use it.
First I tried the Cloud way.
I get to drop down fields.
Devices and Gateways.
Under Gateways my devices will be shown.
But I can’t choose only the Gateway, I have to choose a device too.
The I will get the Message:
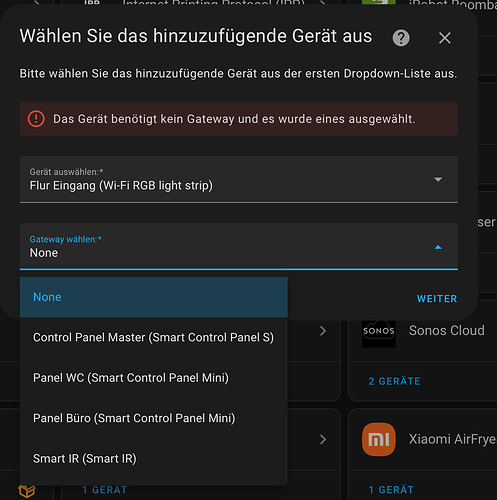
Das Gerät benötigt kein Gateway und es wurde eines ausgewählt.
Okay lets try the local way…
After typing in the ID, local Key and so on… for the Panel I will be asked:
Select the type suitable for your device.
Gerätetyp
- neptun_smart_waterleak
- mypin_6l_videopetfeeder
- basic_ir_remote
- s11_rfir_remote
None of the 4 devices are mine and the Panel will also not be integrated.
I think I make a mistake … but I don’t know where…
Hello,
@Shadowkora can you confirm which Tuya integration did you use because there are several having similar name like LocalTuya Integration, Tuya Local etc.
Thanks
I used the one that Shadowkora posted above.
seems great.
Your goal is to install ESP Home for managing Home Assistant on it ?
Could you take picture or videos ?
Hey @tom101, do you think you could share the tools and process you used to dump the NAND flash? I would like to try to do it myself.
Yes no problem. I used hot air gun to remove the flash. Then used a “wson 8x6 adapter” and a xgecu T48 to read it. I added a little bit of insulation tape to the bottom of the flash chip to prevent the middle soldering pad (used as heat sink I think) from shorting the adapter while reading.
It might well be possible to read it in circuit with the appropriate pogo pin adapter without removing the flash, I didn’t try this though.
Once you have the dump search for “root:” and you’ll find the /etc/passwd files and the /etc/shadow files. You’re looking for the shadow file. You’ll recognise it as it’ll have “root:” then a string of random letters. You’re going to want to use hashcat or similar to crack the password. Every one I’ve done is exactly 8 characters and lowercase letters and numbers only (no uppercase or symbols) which narrows the keyspace significantly. If you need help cracking the passwords send the hashes on here and I’ll get that done for you.
Hope this helps and if you have any questions let me know.
I’ve stalled a bit playing with this one since receiving another switch with 6" screen, physical buttons and android. Would definitely get back to it though as soon as I have time.
anybody? can this TPP06 show on screen temperature? (from data sensor)
Hi,
@tom101
I strugle with cracking the hash from the memory dump, which hashing algorithm did you selected? And can you share the command you used, since I struggle with the syntax of hashcat
Sorry for the late reply. Send me the hashes and I’ll have a crack. You’re limiting your search for a password 8 characters. Only lowercase letters and numbers. Hashmode 1500 off the top of my head but can check later for you.
Hi,
I still can not get this to work, hashcat complaints that the hash is malformed. The hash is $1$QxNje/1B$39KC5gIUyhbc25Kh38eqS.
Thanks for your help
try hashcat mode 500, e.g.
hashcat -m 500 -a 3 -1 ?l?d -w 3 -O --increment-min 8 -i hashfile ?1?1?1?1?1?1?1?1
@matban @tom101
How long did this take you? Hashcat gives me an ETA of 5 days. That’s a lot, for a password with 2,8 billion combinations, in my opinion
Is there a practical way to replace the password hash in the binary, loading it back on to the device and be done.
I though of using an text editor, but I don’t want to break anything. Since the editor I am using is not able to properly read the machine code witch is also included in the binary. I’m worried that it might corrupt the file when I save it
About 20 minutes. I’m out currently but will get this cracked for you tomorrow