I tried, on my experience is that ESP32 out of the box are not powerful enough, and lacks IR for dark environments. I get very bad images. Specially worse if you need to OCR.
So there isn’t any possible way to configure an a9 camera to make my own P2P server for my camera? Y have an A9_L2_V7
I bought this camera in the hope I could make a cheap security system out of it. I first tried ESP32’s but the image quality was horrible. I’m not talking resolution, but it had green and magenta stripes that flickered randomly to the point it wasn’t worth looking at.
Anyways, here is the good stuff:
The camera I am operating on is A9-L2-V7 and is running Thread Operating System 3.1.0 build Aug 19 2021
I was able to communicate with the device over the micro USB port and connect it to a USB to TTL
I am an amateur on hacking devices but I was able to dump part of the flash using the in-device command fal probe. The output of this command gave me a table.
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
With this information, I used the commands fal probe bootloader then fal read *address *length. These commands made it read and paste the output of the flash memory. As this command didn’t give me the ability to write to a file, I had to copy and paste from the putty terminal. This is of itself isn’t horrible, but the device was only able to print out 12KB of data at a time, or else it crashed.
With some copy and paste magic, with along sprinkle of programming to format files, I was able to make some .bin files.
Here are the files:
https://cdn.discordapp.com/attachments/755599394182660136/934028339864297532/A9_cam_dump.zip
I haven’t had the chance to error-check the files, so it might be possible that I didn’t copy and paste a section. I added the raw text so you can check to make sure that the address is in the correct order and without gaps.
Of the three available partitions, the download partition kept just giving errors, so there was no luck of me recovering it. Also, the other partitions that I did get, the end of the partition read was acting weird, It was giving errors such as out of bounds of partition when I know for a fact I was inside. Therefore, the trailing end of the dumps might be missing or incorrect.
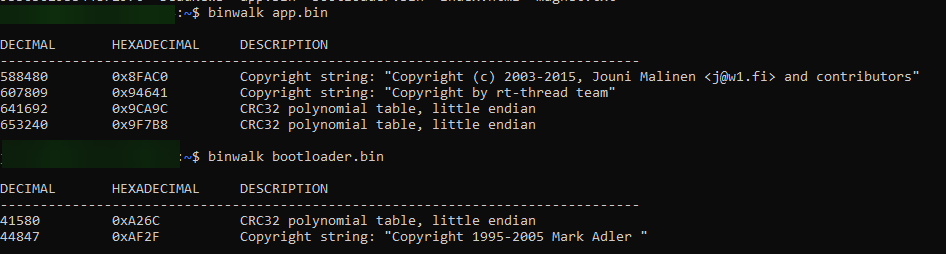
I was able to do a binwalk of the files:
P.S. To stop the device from constantly looking for an AP, type rxsens it shuts it up for some reason.
also, as per the console, the resolution of this device is 640x480, don’t believe any China marketing lies that say it is HD.
I hope this helps someone! 
Very interesting indeed! Can you please elaborate the USB to TTL thing? I cannot figure out how you did it.
The USB to TTL is this device Amazon.com
and how you connect to it, is with this cable 4 Core Mobile Data Cable Micro Usb Type B Extension Cable Male To Dupont 2.54 4pin Connector - Buy Micro Usb Type B Cable,Right Angle 90 Degree,Micro B Extension Cable Product on Alibaba.com
Personally, I just cut up a normal micro USB cable and hooked it up to the USB to TTL, it’s cheaper and faster with the cost of looking nice and ease of use.
Do your own research on where to buy these, I just picked random links to show you. Don’t pay more than $8 for the USB to TTL.
Wow!!! This was completely unknown to me. Lucky enough, I had a USB to TTL device at home but never occurred me to connect the TTL input to a USB port.
Here you go the pinout:
CH340 TTL → Cam USB
- GND → GND (pin 5)
- Vcc → Vcc (pin 1)
- Rx → D+ (pin 3)
- Tx → D- (pin 2)
Then you open Putty and configure it for Serial. Set the corresponding COM port and set speed to 115200, 8 data bits, 1 stop bits, no parity, no flow control. That’s it!
This is what I get:
NOTE: The access point the camera connects to does not have Internet access.
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Feb 25 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1a:c7:12:59:82
[FUNC]rwnxl_init
WAKE GPIO 20 0
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00 000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00 000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001da0d
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041f7f0, adc-buf-len:5120, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3767, total = 3767
[wlan_connect]:start tick = 0, connect done tick = 3767, total = 3767
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 4692, total = 4692
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, no response
1, try:ntp.ntsc.ac.cn, no response
all ntp host are no response
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202102211937, timestamp: 1614236949
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
[E/HTTP_OTA] (http_ota_fw_download:143) open uri failed.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
ota alarm start: 00:30:00
========didApilics:OK len=6====
video open
voide open aready DONE
vi open_p2p
vi open_p2p done
voice open
voice aready opened
play adpcm init
set_dac_sample_rate 8000
[icodec]:open sound device
******* PPCS Version:3010401 ********
Init String:EBGDEJBJKGJLGHJIEJGMFOEGABCDEINDHDABAEGJAFNJOJLKHLAKDMKNHCLMMILCFABCDEHEPPICADCN:@@@@....
@Thulinma do you have any update on publishing your code or at least the decoder for the “encryption” protocol?
It seems like no one else has gotten very far yet with actually getting a video streams out of these things.
Personally my “A9 mini camera” seems to be using an encrypted version of the protocol. The pattern of messages seems somewhat consistent with the “PPPP” protocol you described, but all messages start with 0x5d instead of 0x1f, which I assume means they have some encryption scheme.
looking at the decompiled little stars apk, a tiny bit of info that might be useful:
All the relevant functionality seems to be in object/p2pipcam/nativecaller/NativeCaller.java. The actual implementation of the functions is in lib/*/libobject_jni.so. That includes both C and C++ functions (e.g. PPPP_Initialize and CPPPPChannel::SendSDRecordSetting
The BaseActivity has a StartPPPP function that changes some magic-encryption-looking-value based on the id of the camera: It supports ids starting with ACCQ, THPC, AZQ, ALK, BCCQ.
The StartPPPP function is called with the camera ID (seen in the app), the username, the password, and the hardcoded SystemSerVer magic string.
The only reference to encryption is a function _P2P_Proprietary_Encrypt/Decrypt() in the native library that is referenced from SendMessage and SendMessageLocal and over_time_receive
Some more console dumps.
1) Dump with Little Starts but without Internet connection. Camera and Phone on same LAN. LAN without Internet.
▒
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Feb 25 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1e:b5:12:59:93
[FUNC]rwnxl_init
WAKE GPIO 20 0
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001da0d
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041f7f0, adc-buf-len:5120, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3700, total = 3700
[wlan_connect]:start tick = 0, connect done tick = 3700, total = 3700
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 7689, total = 7689
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, no response
1, try:ntp.ntsc.ac.cn, no response
all ntp host are no response
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202102211937, timestamp: 1614236949
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
[E/HTTP_OTA] (http_ota_fw_download:143) open uri failed.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
ota alarm start: 00:30:00
========didApilics:OK len=6====
video open
voide open aready DONE
vi open_p2p
vi open_p2p done
voice open
voice aready opened
play adpcm init
set_dac_sample_rate 8000
[icodec]:open sound device
******* PPCS Version:3010401 ********
Init String:EBGDEJBJKGJLGHJIEJGMFOEGHFNPDINDHDABAEGJAFNJOJLKHLAKDMKNHCLMMILCFIMIPAHEPPICADCN:@@@@....
0, try:cn.ntp.org.cn, no response
1, try:ntp.ntsc.ac.cn, no response
all ntp host are no response
compare succeed!!!
compare succeed!!!
compare succeed!!!
compare succeed!!!
input:GET /decoder_control.cgi?command=12&onestep=0&&user=admin&pwd=admin&
namebuf:admin,len=5
pswbuf:admin,len=5
compare succeed!!!
app_playback_stop
tvoice init 0001da0d
tvoice aready DONE
video open
voide open aready DONE
app_playback_video_audio_thread_restart
CAMERA HID SET!!
set 320x240 bitrate size
fps_type=1
set FPS OK
compare succeed!!!
input:GET /decoder_control.cgi?command=17&onestep=1&&user=admin&pwd=admin&
namebuf:admin,len=5
pswbuf:admin,len=5
compare succeed!!!
Battery real adc=4106
Battery band=4
output=:var battband=4;
compare succeed!!!
set 640x480 bitrate size
fps_type=1
set FPS OK
===========end online p2p==============
Message
===========end online p2p==============
happens when Little Stars application is closed.
2) Now an interesting one. The setup is the same as previous but now the LAN has Internet access. The goodies here is that I catch an on-going OTA firmware upgrade of the camera. The phone is on the LAN.
▒
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Feb 25 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1e:b5:12:59:93
[FUNC]rwnxl_init
WAKE GPIO 20 0
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001da0d
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041f7f0, adc-buf-len:5120, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3715, total = 3715
[wlan_connect]:start tick = 0, connect done tick = 3716, total = 3716
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 4701, total = 4701
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, get response
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202102211937, timestamp: 1614236949
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
dl_part->name : download
dl_part->flash : beken_onchip
dl_part->offset: 0x00132000
dl_part->len : 835584
[I/HTTP_OTA] OTA file size is (469760)
[I/HTTP_OTA] OTA file raw size 745432 bytes.
[I/HTTP_OTA] OTA file describe partition name app, version: app_202103241937, ti mestamp: 1616551315.
new:app_202103241937, old:app_202102211937
is new
[I/HTTP_OTA] FLASH_PROTECT_HALF.
.Download: [> ] 0%
.Download: [=> ] 1%
.Download: [==> ] 2%
.Download: [===> ] 3%
.Download: [====> ] 4%
.Download: [=====> ] 5%
.Download: [======> ] 6%
.Download: [======> ] 6%
.Download: [=======> ] 7%
.Download: [========> ] 8%
.Download: [=========> ] 9%
.Download: [==========> ] 10%
.Download: [===========> ] 11%
.Download: [============> ] 12%
.Download: [=============> ] 13%
.Download: [=============> ] 13%
.Download: [==============> ] 14%
.Download: [===============> ] 15%
.Download: [================> ] 16%
.Download: [=================> ] 17%
.Download: [==================> ] 18%
.Download: [===================> ] 19%
.Download: [====================> ] 20%
.Download: [====================> ] 20%
.Download: [=====================> ] 21%
.Download: [======================> ] 22%
.Download: [=======================> ] 23%
.Download: [========================> ] 24%
.Download: [=========================> ] 25%
.Download: [==========================> ] 26%
.Download: [===========================> ] 27%
.Download: [===========================> ] 27%
.Download: [============================> ] 28%
.Download: [=============================> ] 29%
.Download: [==============================> ] 30%
.Download: [===============================> ] 31%
.Download: [================================> ] 32%
.Download: [=================================> ] 33%
.Download: [==================================> ] 34%
.Download: [==================================> ] 34%
.Download: [===================================> ] 35%
.Download: [====================================> ] 36%
.Download: [=====================================> ] 37%
.Download: [======================================> ] 38%
.Download: [=======================================> ] 39%
.Download: [========================================> ] 40%
.Download: [========================================> ] 40%
.Download: [=========================================> ] 41%
.Download: [==========================================> ] 42%
.Download: [===========================================> ] 43%
.Download: [============================================> ] 44%
.Download: [=============================================> ] 45%
.Download: [==============================================> ] 46%
.Download: [===============================================> ] 47%
.Download: [===============================================> ] 47%
.Download: [================================================> ] 48%
.Download: [=================================================> ] 49%
.Download: [==================================================> ] 50%
.Download: [===================================================> ] 51%
.Download: [====================================================> ] 52%
.Download: [=====================================================> ] 53%
.Download: [======================================================> ] 54%
.Download: [======================================================> ] 54%
.Download: [=======================================================> ] 55%
.Download: [========================================================> ] 56%
.Download: [=========================================================> ] 57%
.Download: [==========================================================> ] 58%
.Download: [===========================================================> ] 59%
.Download: [============================================================> ] 60%
.Download: [=============================================================> ] 61%
.Download: [=============================================================> ] 61%
.Download: [==============================================================> ] 62%
.Download: [===============================================================> ] 63%
.Download: [================================================================> ] 64%
.Download: [=================================================================> ] 65%
.Download: [==================================================================> ] 66%
.Download: [===================================================================> ] 67%
.Download: [====================================================================> ] 68%
.Download: [====================================================================> ] 68%
.Download: [=====================================================================> ] 69%
.Download: [======================================================================> ] 70%
.Download: [=======================================================================> ] 71%
.Download: [========================================================================> ] 72%
.Download: [=========================================================================> ] 73%
.Download: [==========================================================================> ] 74%
.Download: [==========================================================================> ] 74%
.Download: [===========================================================================> ] 75%
.Download: [============================================================================> ] 76%
.Download: [=============================================================================> ] 77%
.Download: [==============================================================================> ] 78%
.Download: [===============================================================================> ] 79%
.Download: [================================================================================> ] 80%
.Download: [=================================================================================> ] 81%
.Download: [=================================================================================> ] 81%
.Download: [==================================================================================> ] 82%
.Download: [===================================================================================> ] 83%
.Download: [====================================================================================> ] 84%
.Download: [=====================================================================================> ] 85%
.Download: [======================================================================================> ] 86%
.Download: [=======================================================================================> ] 87%
.Download: [========================================================================================> ] 88%
.Download: [========================================================================================> ] 88%
.Download: [=========================================================================================> ] 89%
.Download: [==========================================================================================> ] 90%
.Download: [===========================================================================================> ] 91%
.Download: [============================================================================================> ] 92%
.Download: [=============================================================================================> ] 93%
0, try:cn.ntp.org.cn, get response
.Download: [==============================================================================================> ] 94%
.Download: [===============================================================================================> ] 95%
.Download: [===============================================================================================> ] 95%
.Download: [================================================================================================> ] 96%
.Download: [=================================================================================================> ] 97%
.Download: [==================================================================================================> ] 98%
.Download: [===================================================================================================>] 99%
.Download: [====================================================================================================] 100%
[I/OTA] Verify 'download' partition(fw ver: app_202103241937, timestamp: 1616551315) success.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
reboot system
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Mar 24 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1e:b5:12:59:93
[FUNC]rwnxl_init
WAKE REBOOT
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001dc39
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041a778, adc-buf-len:5888, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3678, total = 3678
[wlan_connect]:start tick = 0, connect done tick = 3678, total = 3678
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 4666, total = 4666
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, get response
[E/NTP]: ERROR select the socket timeout(10s)
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202103241937, timestamp: 1616551315
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
dl_part->name : download
dl_part->flash : beken_onchip
dl_part->offset: 0x00132000
dl_part->len : 835584
[I/HTTP_OTA] OTA file size is (469760)
[I/HTTP_OTA] OTA file raw size 745432 bytes.
[I/HTTP_OTA] OTA file describe partition name app, version: app_202103241937, timestamp: 1616551315.
new:app_202103241937, old:app_202103241937
is old
[E/HTTP_OTA] (http_ota_fw_download:259) no need to updata.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
ota alarm start: 00:30:00
========didApilics:OK len=6====
video open
voide open aready DONE
vi open_p2p
vi open_p2p done
voice open
voice aready opened
play adpcm init
set_dac_sample_rate 8000
[icodec]:open sound device
******* PPCS Version:3010401 ********
Init String:EBGDEJBJKGJLGHJIEJGMFOEGHFNPDINDHDABAEGJAFNJOJLKHLAKDMKNHCLMMILCFIMIPAHEPPICADCN:@@@@....
0, try:cn.ntp.org.cn, get response
compare succeed!!!
compare succeed!!!
compare succeed!!!
compare succeed!!!
compare succeed!!!
compare succeed!!!
input:GET /decoder_control.cgi?command=12&onestep=0&&user=admin&pwd=admin&
namebuf:admin,len=5
pswbuf:admin,len=5
compare succeed!!!
app_playback_stop
tvoice init 0001dc39
tvoice aready DONE
video open
voide open aready DONE
app_playback_video_audio_thread_restart
CAMERA HID SET!!
set 320x240 bitrate size
fps_type=1
set FPS OK
compare succeed!!!
input:GET /decoder_control.cgi?command=17&onestep=1&&user=admin&pwd=admin&
namebuf:admin,len=5
pswbuf:admin,len=5
compare succeed!!!
Battery real adc=4121
Battery band=4
output=:var battband=4;
compare succeed!!!
set 640x480 bitrate size
fps_type=1
set FPS OK
===========end online p2p==============
3) This one here concerns phone on WAN and pressing the buttons on the camera:
button press down
button long press start
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button long press hold
button press up
hold timer=211
stop watch dog
gpio:5,level:1
===index map:20,edge map:20===
---deep sleep test param : 0x20 0x20 0x0 0x0 0 1
▒--enter deep sleep :wake up with gpio 0~31 ps: 0x20 0x20
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Mar 24 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1e:b5:12:59:93
[FUNC]rwnxl_init
WAKE GPIO 20 0
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001dc39
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041a778, adc-buf-len:5888, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3676, total = 3676
[wlan_connect]:start tick = 0, connect done tick = 3676, total = 3676
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 4657, total = 4657
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, get response
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202103241937, timestamp: 1616551315
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
dl_part->name : download
dl_part->flash : beken_onchip
dl_part->offset: 0x00132000
dl_part->len : 835584
[I/HTTP_OTA] OTA file size is (469760)
[I/HTTP_OTA] OTA file raw size 745432 bytes.
[I/HTTP_OTA] OTA file describe partition name app, version: app_202103241937, timestamp: 1616551315.
new:app_202103241937, old:app_202103241937
is old
[E/HTTP_OTA] (http_ota_fw_download:259) no need to updata.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
ota alarm start: 00:30:00
========didApilics:OK len=6====
video open
voide open aready DONE
vi open_p2p
vi open_p2p done
voice open
voice aready opened
play adpcm init
set_dac_sample_rate 8000
[icodec]:open sound device
******* PPCS Version:3010401 ********
Init String:EBGDEJBJKGJLGHJIEJGMFOEGHFNPDINDHDABAEGJAFNJOJLKHLAKDMKNHCLMMILCFIMIPAHEPPICADCN:@@@@....
button press down
button press up
button single click
demo_apcfgctr.state=3!!!!
DEMO_APCFG_START!!!!
video close
voide close
video_transfer_deinit
video_transfer_main exit
camera_intfer_deinit,a5a50003-a5a50005
video_intf_main exit
video close DONE
sta_ip_down
netif_set_link_down !, vif_idx:0
SM_DISCONNECT_IND
RW_EVT=1
RW_EVT_STA_DISCONNECTED-(mac=00:1e:8c:72:2f:82 )
Cancelling scan request
wpa/host apd remove_if:0
app_demo_softap_init
DEMO_APCFG_STA_DISCON!!!
ap: 00:1e:b5:12:59:92,1,0,ACCQ046396NNMPZ,0,
set ip info: 192.168.4.153,255.255.255.0,192.168.4.153
ssid:ACCQ046396NNMPZ key:
Soft_AP_start
[saap]MM_RESET_REQ
[saap]ME_CONFIG_REQ
[saap]ME_CHAN_CONFIG_REQ
[saap]MM_START_REQ
hapd_intf_add_vif,type:3, s:0, id:0
apm start with vif:0
vif_idx:0, ch_idx:0, bcmc_idx:2
uap_ip_start
configuring interface uap (with Static IP)
please use rtthread dncp start server
DHCP server start request 0, try:cn.ntp.org.cn, get response
button press down
button press up
button single click
demo_apcfgctr.state=1!!!!
Stop udp cfg!!!!
reboot system
\ | /
- RT - Thread Operating System
/ | \ 3.1.0 build Mar 24 2021
2006 - 2018 Copyright by rt-thread team
SEARCH PASSWORD FAIL
user cfg MAC:00:1e:b5:12:59:93
[FUNC]rwnxl_init
WAKE REBOOT
deep_ps gpio clear over
[FUNC]calibration_main
get rfcali_mode:0
tssi_th:b-125, g-100
fit n20 tab with dist:2
fit n20 tab with dist:2
fit n20 tab with dist:2
txpwr table for ble ch0/19/39 inused
lpf_i & q in flash is:14, 14
xtal in flash is:8
xtal_cali:8
[FUNC]ps_init
[FUNC]func_init OVER!!!
lwIP-2.0.2 initialized!
set dac vol:65 - indx:11,dig:30,ana:1a
set adc vol: 99 - 99
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register station wlan device sucess!
igmp_mac_filter add 224.0.0.1 01:00:5E:00:00:01
register soft-ap wlan device sucess!
beken wlan hw init
drv_pm_init
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_flash_init:63) Flash device | beken_onchip_crc | addr: 0x00000000 | len: 0x00400000 | blk_size: 0x00001000 |initialized finish.
[D/FAL] (fal_partition_init:176) Find the partition table on 'beken_onchip_crc' offset @0x0000d2cc.
[I/FAL] ==================== FAL partition table ====================
[I/FAL] | name | flash_dev | offset | length |
[I/FAL] -------------------------------------------------------------
[I/FAL] | bootloader | beken_onchip_crc | 0x00001f00 | 0x0000e000 |
[I/FAL] | app | beken_onchip_crc | 0x00010000 | 0x00110000 |
[I/FAL] | download | beken_onchip | 0x00132000 | 0x000cc000 |
[I/FAL] =============================================================
[I/FAL] RT-Thread Flash Abstraction Layer (V0.4.0) initialize success.
TZH customer=2
ROMFS File System initialized!
Enter normal mode...
app_init finished
app_led_init
start watch dog
rt_hw_wdg_start time=10000 threshold=5000
app_demo_apcfg_init 1
PPCScfm DID=ACCQ-046396-NNMPZ
PPCScfm DID_APILICENSE=UHBEAL
Camera name=Camera
User name=admin
User password=admin
SEARCH USER OK ssid=default
SEARCH USER OK key=
st_ssid=default
st_pwd=
ssid:default key:
[sa_sta]MM_RESET_REQ
[sa_sta]ME_CONFIG_REQ
[sa_sta]ME_CHAN_CONFIG_REQ
[sa_sta]MM_START_REQ
hapd_intf_add_vif,type:2, s:0, id:0
wpa_dInit
wpa_supplicant_req_scan
Setting scan request: 0.100000 sec
MANUAL_SCAN_REQ
video open
video_intf_main
video_transfer_init 3
video_transfer_main entry
video transfer send type:3
set 640x480 bitrate size
Camera Reset
fps_type=1
set FPS OK
GC_0309init finish
camera_intfer_init,a5a50003-a5a50005
vbuf opened
sd check init-----
sd_check_init ok!
voice open
tvoice init 0001dc39
tvoice main
set adc sample rate 8000
set adc channel 1
adc-buf:0041a778, adc-buf-len:5888, ch:1
msh />wpa_supplicant_scan
wpa_drv_scan
wpa_send_scan_req
wpa_driver_scan_cb
wpa_get_scan_rst:1
MSG_AP_FOUND!!!
wpa_supplicant_connect
Cancelling scan request
wpa_driver_associate
---------SM_CONNECT_IND_ok
wpa_driver_assoc_cb
[wlan_connect]:start tick = 0, connect done tick = 3689, total = 3689
[wlan_connect]:start tick = 0, connect done tick = 3689, total = 3689
[WLAN_MGNT]wlan sta connected event callback
sta_ip_start
configuring interface mlan (with DHCP client)
dhcp_check_status_init_timer
Cancelling scan request
batt-band=4
IP UP: 192.168.1.226
[ip_up]:start tick = 0, ip_up tick = 4672, total = 4672
=========================
demo_apcfg_sta_ok!!!!
0, try:cn.ntp.org.cn, get response
[E/HTTP_OTA] (http_ota_alarm_start:451) do ota when poweron, and first connected
current firmware name: app, version: app_202103241937, timestamp: 1616551315
remote url:http://112.74.76.191/update_jxl_gc0309/rtthread.rbl
dl_part->name : download
dl_part->flash : beken_onchip
dl_part->offset: 0x00132000
dl_part->len : 835584
[I/HTTP_OTA] OTA file size is (469760)
[I/HTTP_OTA] OTA file raw size 745432 bytes.
[I/HTTP_OTA] OTA file describe partition name app, version: app_202103241937, timestamp: 1616551315.
new:app_202103241937, old:app_202103241937
is old
[E/HTTP_OTA] (http_ota_fw_download:259) no need to updata.
[I/HTTP_OTA] FLASH_PROTECT_ALL.
ota alarm start: 00:30:00
========didApilics:OK len=6====
video open
voide open aready DONE
vi open_p2p
vi open_p2p done
voice open
voice aready opened
play adpcm init
set_dac_sample_rate 8000
[icodec]:open sound device
******* PPCS Version:3010401 ********
Init String:EBGDEJBJKGJLGHJIEJGMFOEGHFNPDINDHDABAEGJAFNJOJLKHLAKDMKNHCLMMILCFIMIPAHEPPICADCN:@@@@....
Oh, hey! I haven’t checked this topic in ages, heh.
I can confirm the device has no H264 encoder on board, so MJPG is all it does. The resolution is also pretty crap. But… it works!
I’ve reached out to the security researcher that helped me figure out how to talk to these things and see if he’s okay with me publishing the code. If he is, you can expect it shorty. (Last I checked he wanted me to wait until he published some stuff first - but that’s now almost a year ago and I imagine that has happened by now…)
What I can already give you is this:
static const char KEY_TABLE[] = {
0x7C, 0x9C, 0xE8, 0x4A, 0x13, 0xDE, 0xDC, 0xB2, 0x2F, 0x21, 0x23, 0xE4, 0x30, 0x7B, 0x3D, 0x8C,
0xBC, 0x0B, 0x27, 0x0C, 0x3C, 0xF7, 0x9A, 0xE7, 0x08, 0x71, 0x96, 0x00, 0x97, 0x85, 0xEF, 0xC1,
0x1F, 0xC4, 0xDB, 0xA1, 0xC2, 0xEB, 0xD9, 0x01, 0xFA, 0xBA, 0x3B, 0x05, 0xB8, 0x15, 0x87, 0x83,
0x28, 0x72, 0xD1, 0x8B, 0x5A, 0xD6, 0xDA, 0x93, 0x58, 0xFE, 0xAA, 0xCC, 0x6E, 0x1B, 0xF0, 0xA3,
0x88, 0xAB, 0x43, 0xC0, 0x0D, 0xB5, 0x45, 0x38, 0x4F, 0x50, 0x22, 0x66, 0x20, 0x7F, 0x07, 0x5B,
0x14, 0x98, 0x1D, 0x9B, 0xA7, 0x2A, 0xB9, 0xA8, 0xCB, 0xF1, 0xFC, 0x49, 0x47, 0x06, 0x3E, 0xB1,
0x0E, 0x04, 0x3A, 0x94, 0x5E, 0xEE, 0x54, 0x11, 0x34, 0xDD, 0x4D, 0xF9, 0xEC, 0xC7, 0xC9, 0xE3,
0x78, 0x1A, 0x6F, 0x70, 0x6B, 0xA4, 0xBD, 0xA9, 0x5D, 0xD5, 0xF8, 0xE5, 0xBB, 0x26, 0xAF, 0x42,
0x37, 0xD8, 0xE1, 0x02, 0x0A, 0xAE, 0x5F, 0x1C, 0xC5, 0x73, 0x09, 0x4E, 0x69, 0x24, 0x90, 0x6D,
0x12, 0xB3, 0x19, 0xAD, 0x74, 0x8A, 0x29, 0x40, 0xF5, 0x2D, 0xBE, 0xA5, 0x59, 0xE0, 0xF4, 0x79,
0xD2, 0x4B, 0xCE, 0x89, 0x82, 0x48, 0x84, 0x25, 0xC6, 0x91, 0x2B, 0xA2, 0xFB, 0x8F, 0xE9, 0xA6,
0xB0, 0x9E, 0x3F, 0x65, 0xF6, 0x03, 0x31, 0x2E, 0xAC, 0x0F, 0x95, 0x2C, 0x5C, 0xED, 0x39, 0xB7,
0x33, 0x6C, 0x56, 0x7E, 0xB4, 0xA0, 0xFD, 0x7A, 0x81, 0x53, 0x51, 0x86, 0x8D, 0x9F, 0x77, 0xFF,
0x6A, 0x80, 0xDF, 0xE2, 0xBF, 0x10, 0xD7, 0x75, 0x64, 0x57, 0x76, 0xF3, 0x55, 0xCD, 0xD0, 0xC8,
0x18, 0xE6, 0x36, 0x41, 0x62, 0xCF, 0x99, 0xF2, 0x32, 0x4C, 0x67, 0x60, 0x61, 0x92, 0xCA, 0xD3,
0xEA, 0x63, 0x7D, 0x16, 0xB6, 0x8E, 0xD4, 0x68, 0x35, 0xC3, 0x52, 0x9D, 0x46, 0x44, 0x1E, 0x17
};
static void encrypt(char * buff, const char * key, size_t len){
char prevByte = 0;
for (size_t i = 0; i < len; ++i){
size_t idx = (key[prevByte & 0x03] + prevByte) & 0xFF;
prevByte = buff[i] ^= KEY_TABLE[idx];
}
}
static void decrypt(char * buff, const char * key, size_t len){
char prevByte = 0;
for (size_t i = 0; i < len; ++i){
size_t idx = (key[prevByte & 0x03] + prevByte) & 0xFF;
prevByte = buff[i];
buff[i] ^= KEY_TABLE[idx];
}
}
For the “Little Stars” cameras, use decryption/encryption key 0xB8489000.
The good thing I see is that it seems the camera can be hacked using OTA to upload a different firmware onto it if it is so we can get hold of it.
Sniffing shows Little Stars broadcasts a UDP packet with payload 5d782818 to port 32108 to which the camera responses.
I guess by using the dec/enc key above the negotiation could be decoded (?).
A beta add-on release could be having it to emulate the Little Stars negotiation protocol to get the camera streaming to HA. Still the keep-alive aspect to deal with. Configuring the DNS or IP table on the router pointing back to HA could be an option. The HA add-on would response to this request to avoid the camera rebooting.
Nobody is stopping you! My parseltongue is not great, but the algorithm is simple enough that I think any decent python coder could whip something up using my C example in very little time. 
Yup, you can use the above code and key to decrypt/encrypt that negotiation. It uses the P2P protocol that I linked to earlier in this topic, with as only change that it’s encrypted using this algorithm. It’s not very hard with the P2P protocols docs + this algorithm to implement it all, as the protocol itself is pretty simplistic. And my full code will be released soonish, if all goes well… which handles most of this already.
I’m a fairly decent python coder, but my C language skills are a bit rusty 
So even though I could make a python script easily, I have to understand what the C version does first!
edit: Turns out, the bitwise operators are a simple one-to-one conversion. So making it into python was fairly easy.
import sys
KEY_TABLE = [
0x7C, 0x9C, 0xE8, 0x4A, 0x13, 0xDE, 0xDC, 0xB2, 0x2F, 0x21, 0x23, 0xE4, 0x30, 0x7B, 0x3D, 0x8C,
0xBC, 0x0B, 0x27, 0x0C, 0x3C, 0xF7, 0x9A, 0xE7, 0x08, 0x71, 0x96, 0x00, 0x97, 0x85, 0xEF, 0xC1,
0x1F, 0xC4, 0xDB, 0xA1, 0xC2, 0xEB, 0xD9, 0x01, 0xFA, 0xBA, 0x3B, 0x05, 0xB8, 0x15, 0x87, 0x83,
0x28, 0x72, 0xD1, 0x8B, 0x5A, 0xD6, 0xDA, 0x93, 0x58, 0xFE, 0xAA, 0xCC, 0x6E, 0x1B, 0xF0, 0xA3,
0x88, 0xAB, 0x43, 0xC0, 0x0D, 0xB5, 0x45, 0x38, 0x4F, 0x50, 0x22, 0x66, 0x20, 0x7F, 0x07, 0x5B,
0x14, 0x98, 0x1D, 0x9B, 0xA7, 0x2A, 0xB9, 0xA8, 0xCB, 0xF1, 0xFC, 0x49, 0x47, 0x06, 0x3E, 0xB1,
0x0E, 0x04, 0x3A, 0x94, 0x5E, 0xEE, 0x54, 0x11, 0x34, 0xDD, 0x4D, 0xF9, 0xEC, 0xC7, 0xC9, 0xE3,
0x78, 0x1A, 0x6F, 0x70, 0x6B, 0xA4, 0xBD, 0xA9, 0x5D, 0xD5, 0xF8, 0xE5, 0xBB, 0x26, 0xAF, 0x42,
0x37, 0xD8, 0xE1, 0x02, 0x0A, 0xAE, 0x5F, 0x1C, 0xC5, 0x73, 0x09, 0x4E, 0x69, 0x24, 0x90, 0x6D,
0x12, 0xB3, 0x19, 0xAD, 0x74, 0x8A, 0x29, 0x40, 0xF5, 0x2D, 0xBE, 0xA5, 0x59, 0xE0, 0xF4, 0x79,
0xD2, 0x4B, 0xCE, 0x89, 0x82, 0x48, 0x84, 0x25, 0xC6, 0x91, 0x2B, 0xA2, 0xFB, 0x8F, 0xE9, 0xA6,
0xB0, 0x9E, 0x3F, 0x65, 0xF6, 0x03, 0x31, 0x2E, 0xAC, 0x0F, 0x95, 0x2C, 0x5C, 0xED, 0x39, 0xB7,
0x33, 0x6C, 0x56, 0x7E, 0xB4, 0xA0, 0xFD, 0x7A, 0x81, 0x53, 0x51, 0x86, 0x8D, 0x9F, 0x77, 0xFF,
0x6A, 0x80, 0xDF, 0xE2, 0xBF, 0x10, 0xD7, 0x75, 0x64, 0x57, 0x76, 0xF3, 0x55, 0xCD, 0xD0, 0xC8,
0x18, 0xE6, 0x36, 0x41, 0x62, 0xCF, 0x99, 0xF2, 0x32, 0x4C, 0x67, 0x60, 0x61, 0x92, 0xCA, 0xD3,
0xEA, 0x63, 0x7D, 0x16, 0xB6, 0x8E, 0xD4, 0x68, 0x35, 0xC3, 0x52, 0x9D, 0x46, 0x44, 0x1E, 0x17
]
def encrypt(buff, key):
previousByte = 0
for position, _ in enumerate(buff):
index = (key[previousByte & 0x03] + previousByte) & 0xFF
buff[position] ^= KEY_TABLE[index]
previousByte = buff[position]
return buff
def decrypt(buff, key):
previousByte = 0
for position, _ in enumerate(buff):
index = (key[previousByte & 0x03] + previousByte) & 0xFF
previousByte = buff[position]
buff[position] ^= KEY_TABLE[index]
return buff
if __name__ == "__main__":
key = bytearray(0xB8489000)
if len(sys.argv) == 1:
# Debug code here
InputValue = bytearray("Hello World","ASCII")
print("input:",InputValue)
encrypted = encrypt(InputValue, key)
print("Encrypted Output:", encrypted)
decrypted = decrypt(encrypted, key)
print("Decrypted Output:", decrypted)
exit(0)
if sys.argv[1] == 'encrypt':
print(encrypt(bytearray(sys.argv[2],"ASCII"), key))
if sys.argv[1] == 'decrypt':
print(decrypt(bytearray(sys.argv[2],"ASCII"), key))
Here is the code in python, variables buff and key need to be a bytearray() object.
I don’t have real data to truly know if this is bug free, but I can confirm that it at least decrypt its own encryption.
Keeping it in C is preferred because of memory and speed.
@Thulinma please let us know if you can release that code or the documentation. I can try adapting the library for it once I have enought information.
I have a Wireshark file containing the result of the sniffing.
192.168.1.1 router
192.168.1.226 camera (A9)
192.168.1.135 my mobile phone running Little Stars
The network (router) does not have Internet access.
Unfortunately I cannot upload it herein because only picture files are permitted (and format checked). Let me know if you would like me to upload it somewhere else.
Some more info:
Little Stars broadcast to find the camera starts on line 166.
Camera’s response line 171.
@combe15 I have tried a couple of strings happening during the handshake. I do not get anything human readable.
Looks like I’ll be able to share the full code around the second half of February! That also includes a pretty-printing debug tool for analysing/decrypting payloads.
In the meanwhile, this documents the various commands you can send/receive pretty well: iot/pppp.fdesc at f02b4d7e143a369d87c40dfe80944366d1113b81 · pmarrapese/iot · GitHub
Thanks also go to the author of that repository for helping me with the encode/decode functions!
If somebody wants to implement the protocol before I release mine, here is how to do it in plain English (keep the message format from the above URL handy to look up message formats!):
The general process is to first send a MSG_LAN_SEARCH message on the 255.255.255.255 broadcast address, port 32108. That’s local LAN discovery, and preferred as the protocol itself is a massive security hole and you probably want to make the camera unable to access the internet. If no replies are received, contact a well-known server with a MSG_HELLO message instead (there are several for each camera brand, use wireshark to collect some IP addresses), and it will set up the connection to the camera for you.
If you receive MSG_PUNCH_PKT, respond with the same message back.
If you receive MSG_P2P_RDY, send a MSG_ALIVE followed by a MSG_DRW message containing the name and password of the camera and another MSG_DRW message containing the request to start streaming.
If you receive MSG_HELLO_ACK, respond with MSG_P2P_REQ.
If you receive MSG_PUNCH_TO, parse the content and continue by sending MSG_PUNCH_PKT to the IP/port listed in the message.
If you receive MSG_ALIVE, respond with MSG_ALIVE_ACK.
If you receive MSG_CLOSE, stop sending data - the camera has closed the session.
If you receive MSG_DRW, that’s interesting data! Respond with MSG_DRW_ACK to acknowledge receipt, and parse the contents. Requests/responses follow a HTTP-like scheme, and video data can be recognized by the 6th byte being 0x01.
For video, throw away the 8 byte header and keep the rest. If it starts with 0x55AA, this is the start of a new frame and the first 32 bytes are the frame header. Bytes 16 and 17 contain the frame size in bytes, little-endian format. Bytes 12 and 13 contain the frame number, again little-endian. Bytes 8-11 contain the unix time at time of sending, little-endian. Everything that follows is raw frame data, which is just a JPG image. Non-header packets can just be appended to your frame buffer until frame-size bytes have been received, and your JPG is complete.
Wash, rinse, repeat. These cameras only do JPG, and only support 320x240 and 640x480 resolutions.
Here are some MSG_DRW commands you can send to the camera that I discovered with some trial and error:
GET //decoder_control.cgi?command=15&onestep=1 <- IR on
GET //decoder_control.cgi?command=15&onestep=0 <- IR off
GET //decoder_control.cgi?command=12&onestep=1 <- 320x240 resolution
GET //decoder_control.cgi?command=13&onestep=1 <- 640x480 resolution
GET //decoder_control.cgi?command=10&onestep=1 <- vertical flip (toggle)
GET //decoder_control.cgi?command=8&onestep=1 <- horizontal flip (toggle)
Have fun and good luck!