Hi @xero08 Welcome and thanks for waking me up on this!
I’ve been pondering the PR comments and responded here
I’m sure tests could show how much time ip_address creation takes but as there’s no option if you want to check if an ip address is in a subnet I believe it is a price worth taking.
FWIW I’ve ~50 subnets in my config and I don’t notice any access time problems.
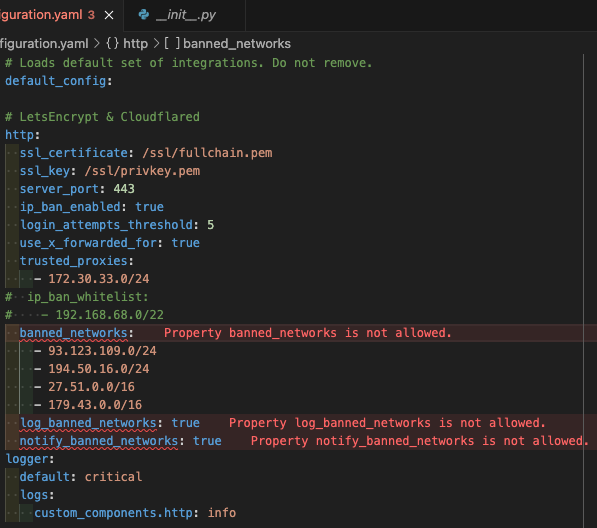
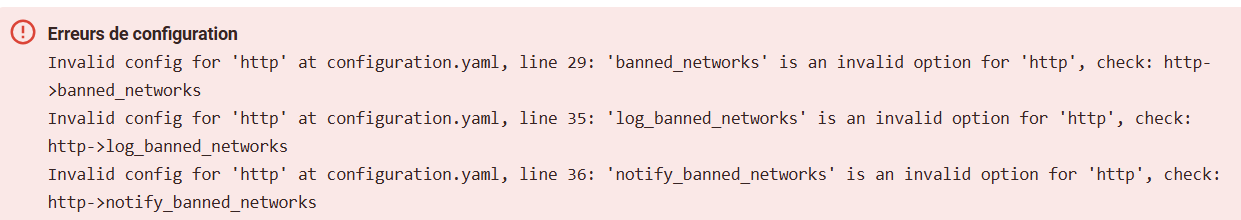
In the configuration.yaml: it shows "Property banned_network is not allowed as per the above attachment.
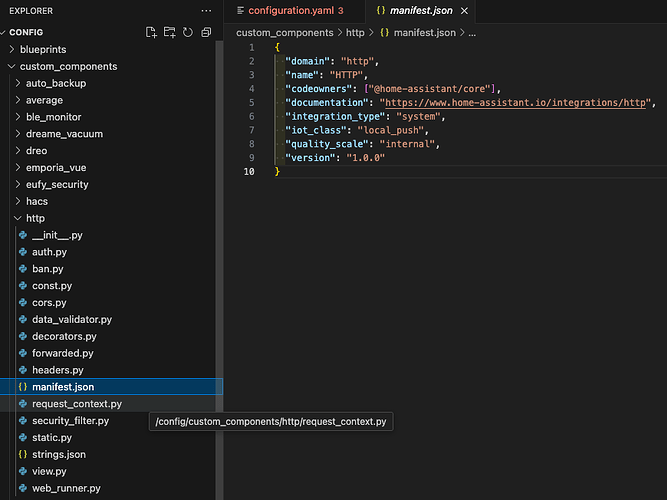
Version 1.0.0 is updated in the manifest.json as instructed.
Welcome @sakanaou
Are you saying it does not work for you?
The screenshots look like VSCode so I’m not sure why it’s telling you that the properties are not allowed. Maybe it’s checking them against the HA base code and not my fork?
Does it not work in Home Assistant as a custom component?
What’s in your HA logs?
Hi,
Did you restart HA after adding the files to custom_components/http? I had a simular issue before restarting.
I have the same issue.
all files copied in custom_components/http
HA rebooted (not restarted)
When I add the lines
banned_networks: # Make sure the format is right, e.g. /16 must end in 0.0/16
- 111.7.0.0/16
- 45.0.0.0/8
- 179.43.0.0/16
- 123.160.0.0/14
- 195.178.0.0/16
log_banned_networks: True # optional as defaults to True
notify_banned_networks: True # optional as defaults to True
And I press “verify”, I get an error for the 3 values
When adding version in manifest.json, have u double checked that format is correct? (A comma-sign is needed at the end of the previous line)
Is there anything in the HA log saying it couldn’t load the http custom component at boot time?
Thx, I forgot the comma on line “quality_scale” just before version
I’m not sure most people realise the continuous bot hacking attempts taking place from all over the world
FWIW my banned list now looks like this:
- 8.128.0.0/11 # China
- 8.208.0.0/12 # Singapore
- 34.0.0.0/8 # USA Google cloud users
- 35.192.0.0/12 # Google cloud users
- 36.96.0.0/11 # China
- 39.0.0.0/8 # China, Korea, Pakistan, taiwan
- 40.160.8.0/22 # USA
- 43.0.0.0/8 # China
- 47.0.0.0/8 # USA (inc alibaba and vodaphone)
- 62.210.0.0/17 # France
- 45.0.0.0/8
- 51.158.0.0/16
- 51.159.0.0/16
# - 64.226.64.0/18 # Digital Ocean USA
- 64.0.0.0/8 # USA, Canada
- 88.214.0.0/16
- 92.255.85.0/24 # Hong Kong ssh hacking
- 93.0.0.0/8 # Russia, Italy, France, Germany
- 95.111.224.0/20 # Johannes Selg Germany
- 101.0.0.0/8 # China New Zealand Taiwan India
- 103.0.0.0/8 # Asia
- 104.234.189.0/24 # Brazil
- 110.41.0.0/16
- 111.0.0.0/8 # China Taiwan Japan
- 112.0.0.0/10 # China mobile
- 117.0.0.0/8 # China, Vietnam, India
- 119.4.0.0/14 # China
- 120.0.0.0/8 #China, Taiwan...
- 122.51.0.0/16
- 123.160.0.0/14
- 129.144.0.0/12 # Oracle
- 130.61.0.0/16 # Oracle
- 137.220.0.0/16
- 139.196.0.0/16
- 150.5.0.0/16
- 150.136.0.0/16 # Oracle Cloud
- 150.230.0.0/16
- 154.0.0.0/8 # Hong Kong + south afruca + usa
- 158.58.0.0/16 # Iran
- 158.160.0.0/16 # Russia
- 171.0.0.0/8 # Vietnam, China, Thailand, Bank of America
- 179.43.0.0/16
- 180.0.0.0/8 # Asia
- 185.42.12.0/24 # Russia ssh hacking
- 185.213.0.0/16
- 193.0.0.0/8 # Europe
- 195.178.0.0/16
- 196.0.0.0/8 # Africa
- 205.168.0.0/14 #USA
- 212.252.0.0/15 # Turkey
- 216.10.0.0/16
- 223.130.0.0/16
Scary or what?
I agree and hope ban by subnet gets implemented in HA. I’m quite new to HA, but was surprised this feature doesn’t already exists. It’s a great (and simple) way to increase security!
Thanks for this- it has my vote to be implemented into the core
Since I upgraded to 2025.9, the custom http component seems to be ignored.
@tschiex Thanks for letting me know
Looks like time to jump through the hoops again
I’ll dig out my development environment and have a look.
Thank you Mike. I feel bare naked w/o my custom http component ![]()
OK
I’ve got 2025.9.1 up on a VM, added my http component and yes, you’re right, it loads OK , reports blocking blocked sites/subnets but doesn’t actually block them.
I’ve run out of time today but I will pursue this - please be patient
Actually my last post is wrong.
It still does block banned subnets for me - I was fooled by not refreshing my browser cache.
@tschiex will you add the following to the logger section of configuration.yaml and post your ha log so we can see what’s happening at startup and when ha is accessed
logger:
logs:
custom_components.http: debug
@Sonosy Mike, I’m currently away from home for one week. I have the subnet http code in the custom_components folder (where it was and has always been) and when I upgraded, it simply stopped working, saying that the “banned_networks” was an invalid keyword. HA stopped booting and I had to remove all http-subnet keywords from my configuration.
Unfortunately the HA core team has rejected the pull request as they believe
“unfortunately concluded this feature does not belong in Home Assistant core.”
and have closed the pull request and the documentation pull request
There’s no explanation as to why it was rejected so I have asked for the reasoning behind the decision to see if there’s a compromise.
Any ideas?
See the edit here for the reply I received from Erik
I’m having a look at the crowdsec addon as an alternative to modding the http component but I haven’t got anywhere with it yet.
Has anybody used it sccessfully to ban subnets/ip ranges?
<rant>
Respectfully, the reply in that edit is misleading. You can already add individual IP addresses manually, so saying it’s not user configurable is a reductionist approach at best.
Saying “we don’t see firewall type functionality as something we want to implement” is also a moot point. If users can manually add individual entries to the ipbans.yaml, then the platform is already acting as a firewall. All this PR does is avoid the hassle of having to key them in individually or having to set up & maintain a separate addon just for that functionality.
Declaring that privacy is one of your fundamental principles and then rejecting something which makes it easier to prevent bots from intrusion attempts sounds a bit contradictory to me.
</rant>
Wanted to post the above in the PR, but now that it’s been closed it’s futile. Not sure if there’s some way of appealing the decision, but feel free to copy any/all of the above in your counter argument if you wanna make one.