This marks the first fully stable release of fEVR which works alongside Frigate to provide an easy to use object detection system!
An updated Home Assistant Add-On will be available by the end of July 2022.
fEVR works along side of frigate to collect video and snapshots of objects detected using your existing camera systems.

fEVR v0.6 Screenshots
Own Your Home’s Security
fEVR allows you to own your home’s camera system. Instead of paying multiple cloud providers varying rates to perform object detection and recording, bring them all into fEVR in your very own open source self-hosted solution! Google, Wyze, Ring, and varying Tuya based cameras all use your data AND want to charge you to store it in the cloud.
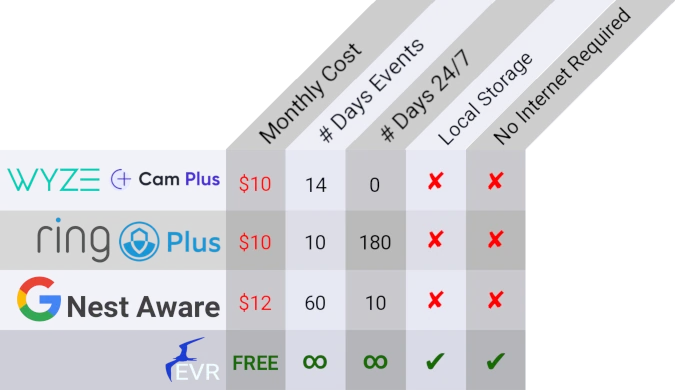
Feature comparison to leading cloud event detection providers
Requirements:
- Frigate fully setup and working
- MQTT Broker (if you have frigate running, you have this) listening to 0.0.0.0
- This caused me many headaches, hopefully it saves you some hair pulling.
It allows mqtt clients on different subnets to access the broker.
If setup within your local lan this does not alone open up external access, only to other subnets which already have access. - Example mosquitto.conf listener section if using port 1883
listener 1883 0.0.0.0
- This caused me many headaches, hopefully it saves you some hair pulling.
Optional but nice:
- Tailscale Account (for secure remote access)
Support
Please note, I will generally answer questions within 24 hours, and most times even faster unless I’m on vacation or going on adventures with the family.
Any abuse, harassment, bullying, or just being mean about a free project that I do in my spare time will get you blocked and reported. I have no tolerance for this.
-
- Information, tutorials and documentation
-
- This is the preferred method if you find an error in the code or something that crashes fEVR.
-
- For discussing configuration issues or things that bug you (UI tweaks or process improvements)
-
- For troubleshooting, a quick question, or you just want to say hi!
-
- Any tier of monthly sponsorship will get you priority support and a mention in the README

