gislis2
July 14, 2020, 6:59pm
1
Hi
Been using Hassio via Raspberry Pi and decided to do a fresh install on a more powerful host with containers and behind Traefik reverse proxy
Everything is working well except setting up the iOS app connection. I am running iOS 14 (18A5319i)
Two issues:
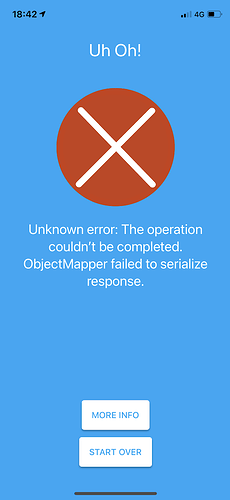
Autodiscovery finds the instance, but when I choose it I get this error when it seems to try authenticating:
ObjectMapper failed to serialize response.
Edit: The picture shows 4G but tried wifi with 4G disabled with same results
When I go the manual way the app crashes when I click the typebox
The app was working fine on iOS14 before I made the switch to docker.docs troubleshooting and even tried to set up Nabu Casa Cloud connection for outside connection (manually entering IP fails per problem .2)
Get the same problem with ipadOS14
Anyone know what could be the issue?
gislis2
July 15, 2020, 6:30pm
2
Found the problem!
Thanks to the inspiration from WhatPlantsCrave here I found the problem not in TLS version but Google Oauth.
here is my working setup for the future. Ofcourse still a work in progress and open for suggestionsheavily based on their Traefik Oauth guide and I wouldn’t have gotten this far without them)
Running Traefik v2 in docker-compose, on a NUC machine Ubuntu Server 20.04
docker-compose.yml
version: '3.8'
services:
#? NETWORK CONTAINERS # # # # # # # # # # # # # # #
#? Traefik Reverse Proxy
traefik:
container_name: traefik
hostname: traefik
image: traefik
restart: unless-stopped
security_opt:
- no-new-privileges:true
networks:
- t2_proxy
ports:
- target: 80
published: 80
protocol: tcp
mode: host
- target: 443
published: 443
protocol: tcp
mode: host
- target: 8080
published: 8080
protocol: tcp
mode: host
volumes:
- /var/run/docker.sock:/var/run/docker.sock:ro
- /etc/localtime:/etc/localtime:ro
- $DOCKERDIR/traefik/acme/acme.json:/acme.json
- $DOCKERDIR/traefik/shared:/shared
- $DOCKERDIR/traefik/rules:/rules
- $DOCKERDIR/traefik/traefik.log:/traefik.log
- $DOCKERDIR/traefik:/etc/traefik
environment:
- CF_API_EMAIL=$CLOUDFLARE_EMAIL
- CF_API_KEY=$CLOUDFLARE_API_KEY
labels:
- "traefik.enable=true"
#? HTTP-to-HTTPS Redirect
- "traefik.http.routers.http-catchall.entrypoints=http"
- "traefik.http.routers.http-catchall.rule=HostRegexp(`{host:.+}`)"
- "traefik.http.routers.http-catchall.middlewares=redirect-to-https"
- "traefik.http.middlewares.redirect-to-https.redirectscheme.scheme=https"
#? HTTP Routers
- "traefik.http.routers.traefik-rtr.entrypoints=https"
- "traefik.http.routers.traefik-rtr.rule=Host(`traefik.$DOMAINNAME`)"
- "traefik.http.routers.traefik-rtr.tls=true"
- "traefik.http.routers.traefik-rtr.tls.domains[0].main=$DOMAINNAME"
- "traefik.http.routers.traefik-rtr.tls.domains[0].sans=*.$DOMAINNAME"
#? Services - API
- "traefik.http.routers.traefik-rtr.service=api@internal"
#? Middlewares
- "traefik.http.routers.traefik-rtr.middlewares=chain-oauth@file"
#? Google OAuth - Proxy layer using Oauth 2.0
oauth:
container_name: oauth
image: thomseddon/traefik-forward-auth:latest
restart: unless-stopped
networks:
- t2_proxy
security_opt:
- no-new-privileges
environment:
- CLIENT_ID=$GOOGLE_CLIENT_ID
- CLIENT_SECRET=$GOOGLE_CLIENT_SECRET
- SECRET=$OAUTH_SECRET
- COOKIE_DOMAIN=$DOMAINNAME
- INSECURE_COOKIE=false
- AUTH_HOST=oauth.$DOMAINNAME
- URL_PATH=/_oauth
- WHITELIST=$MY_EMAIL
- LOG_LEVEL=info
- LOG_FORMAT=text
- LIFETIME=2592000 # 30 days
labels:
- "traefik.enable=true"
#? HTTP Routers
- "traefik.http.routers.oauth-rtr.entrypoints.https"
- "traefik.http.routers.oauth-rtr.rule=Host(`oauth.$DOMAINNAME`)"
- "traefik.http.routers.oauth-rtr.tls=true"
#? HTTP Services
- "traefik.http.routers.oauth-rtr.service=oauth-svc"
- "traefik.http.services.oauth-svc.loadbalancer.server.port=$OAUTH_PORT"
#? Middlewares
- "traefik.http.routers.oauth-rtr.middlewares=chain-oauth@file"
#? APP CONTAINERS # # # # # # # # # # # # # # #
homeassistant:
container_name: homeassistant
image: homeassistant/home-assistant:latest
restart: always
security_opt:
- no-new-privileges
privileged: true
network_mode: host
ports:
- target: 8123
published: $HOMEASSISTANT_PORT
protocol: tcp
mode: host
#devices:
# - /dev/ttyUSB0:/dev/ttyUSB0
# - /dev/ttyACM0:/dev/ttyACM0
volumes:
- $DOCKERDIR/homeassistant:/config
- /etc/localtime:/etc/localtime:ro
- /var/run/docker.sock:/var/run/docker.sock # For Docker Monitor https://github.com/Sanderhuisman/docker_monitor
environment:
- TZ=$TZ
traefik.yml (dynamic conf under $DOCKERDIR/traefik/traefik.yml)
entryPoints:
traefik:
address: ":8080"
http:
address: ":80"
https:
address: ":443"
forwardedHeaders:
trustedIPs:
#* Allow these IPs to set the X-Forwarded-* headers - Cloudflare IPs: https://www.cloudflare.com/ips/
- 173.245.48.0/20
- 103.21.244.0/22
- 103.22.200.0/22
- 103.31.4.0/22
- 141.101.64.0/18
- 108.162.192.0/18
- 190.93.240.0/20
- 188.114.96.0/20
- 197.234.240.0/22
- 198.41.128.0/17
- 162.158.0.0/15
- 104.16.0.0/12
- 172.64.0.0/13
- 131.0.72.0/22
#tls:
#options:
#default:
#minVersion: VersionTLS12
#mintls13:
#minVersion: VersionTLS13
certificatesResolvers:
dns-cloudflare:
acme:
email: $CLOUDFLARE_EMAIL
storage: /acme.json
dnsChallenge:
provider: cloudflare
resolvers:
- "1.1.1.1:53"
- "1.0.0.1:53"
log:
level: ERROR # (Default: error) DEBUG, INFO, WARN, ERROR, FATAL, PANIC
accessLog:
filePath: /traefik.log
bufferingSize: 100 # A buffer of 100 lines
filters:
statusCodes:
- "400-499"
api:
dashboard: true
ping: {}
finally the middlewares.yml and middleware-chain.yml under $DOCKERDIR/traefik/rules
http:
middlewares:
#? Basic Auth which uses a static login from .htpasswd file
middlewares-basic-auth:
basicAuth:
realm: "Traefik2 Basic Auth"
usersFile: "/shared/.htpasswd"
#? Denies request floods (DDoS and CredScan)
middlewares-rate-limit:
rateLimit:
average: 100
burst: 50
#? Security headers for. Headers are the "shipping box" around the website that tells the browser how to handle each component
middlewares-secure-headers:
headers:
accessControlAllowMethods:
- GET
- OPTIONS
- PUT
accessControlMaxAge: 100
hostsProxyHeaders:
- X-Forwarded-Host
sslRedirect: true
stsSeconds: 63072000
stsIncludeSubdomains: true
stsPreload: true
forceSTSHeader: true
customFrameOptionsValue: "allow-from https:$DOMAINNAME"
contentTypeNosniff: true
browserXssFilter: true
# sslForceHost: true
# sslHost: "$DOMAINNAME"
referrerPolicy: "same-origin"
# Setting contentSecurityPolicy is more secure but it can break things. Proper auth will reduce the risk.
# the below line also breaks some apps due to 'none' - sonarr, radarr, etc.
# contentSecurityPolicy = "frame-ancestors '*.example.com:*';object-src 'none';script-src 'none';"
featurePolicy: "camera 'none'; geolocation 'none'; microphone 'none'; payment 'none'; usb 'none'; vr 'none';"
customResponseHeaders:
X-Robots-Tag: "none,noarchive,nosnippet,notranslate,noimageindex,"
server: ""
#? Google Oauth authentication.
middlewares-oauth:
forwardAuth:
address: "http://oauth:4181"
trustForwardHeader: true
authResponseHeaders:
- "X-Forwarded-User"
http:
middlewares:
chain-no-auth:
chain:
middlewares:
- "middlewares-rate-limit"
- "middlewares-secure-headers"
chain-basic-auth:
chain:
middlewares:
- "middlewares-basic-auth"
- "middlewares-rate-limit"
- "middlewares-secure-headers"
chain-oauth:
chain:
middlewares:
- "middlewares-rate-limit"
- "middlewares-secure-headers"
- "middlewares-oauth"
SawKyrom
February 2, 2021, 2:37am
3
Anyone else receiving this error should check that their router or gateway IP is not listed in the IP ban file of the configuration. I had the exact same scenario as @gislis2 , but the cause somewhat different and resolution very simple: comment out or remove the IP ban address in file mentioned previously. Worked immediately after making this observation and change. Hope this helps someone else out there. Cheers!