Hi all,
I had an apache reverse proxy working just fine but when I updated to the latest HA version on pip I now cannot access Lovelace.
I get a 400 Bad Request error. Did something change in the new update?
Hi all,
I had an apache reverse proxy working just fine but when I updated to the latest HA version on pip I now cannot access Lovelace.
I get a 400 Bad Request error. Did something change in the new update?
I see now that I need to have the use_x_forwarded_for option set to true and also the trusted proxies.
The error I’m getting in HA is as follows:
“Received X-Forwarded-For header from an untrusted proxy ::1”
However, when I add ::1 to the list of trusted proxies it doesn’t solve the problem. I’m still getting the same error.
http:
use_x_forwarded_for: true
trusted_proxies:
- ::1
Any thoughts?
I retyped the whole config and it fixed it. I have no idea what was wrong, but now node-red is having issues. I’ll set up a new thread
Hi, I have exactly the same issue, but retype did not work  . Can you please share your working config from apache? Thanks!
. Can you please share your working config from apache? Thanks!
See below
<VirtualHost *:80>
ServerName hass.domain.com
Redirect permanent / https://hass.domain.com/
</VirtualHost>
<VirtualHost *:443>
ServerName hass.domain.com
SSLEngine on
SSLProtocol all -SSLv2 -SSLv3
SSLProxyEngine On
RequestHeader set Front-End-Https "On"
ProxyPreserveHost On
RewriteEngine on
#CacheDisable *
SSLCipherSuite EECDH+AESGCM:EDH+AESGCM:AES256+EECDH:AES256+EDH
SSLHonorCipherOrder on
SSLCertificateFile /etc/letsencrypt/live/domain.com/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/domain.com/privkey.pem
ProxyRequests Off
ProxyPreserveHost on
DocumentRoot "/var/www"
<Directory />
SSLRequireSSL
SSLRequire %{HTTP_HOST} eq "hass.domain.com"
SSLOptions +FakeBasicAuth +StrictRequire
#SSLRequire %{SSL_CIPHER_USEKEYSIZE} >= 128
ErrorDocument 403 https://hass.domain.com
Options FollowSymLinks
AllowOverride None
</Directory>
<Directory /var/www/>
SSLRequireSSL
SSLRequire %{HTTP_HOST} eq "hass.domain.com"
SSLOptions +FakeBasicAuth +StrictRequire
#SSLRequire %{SSL_CIPHER_USEKEYSIZE} >= 128
ErrorDocument 403 https://hass.domain.com
Options Indexes FollowSymLinks MultiViews
AllowOverride All
Order allow,deny
allow from all
</Directory>
ProxyPass /api/websocket ws://localhost:8123/api/websocket
ProxyPassReverse /api/websocket ws://localhost:8123/api/websocket
ProxyPass / http://localhost:8123/
ProxyPassReverse / http://localhost:8123/
RewriteEngine on
RewriteOptions inherit
RewriteCond %{HTTP:Upgrade} =websocket [NC]
RewriteRule /(.*) ws://localhost:8123/$1 [P,L]
RewriteCond %{HTTP:Upgrade} !=websocket [NC]
RewriteRule /(.*) http://localhost:8123/$1 [P,L]
</VirtualHost>
FYI, after looking at my config I realize it’s highly outdated in terms of recommended SSLProtocol and CipherSuites.
You might want to read through this on how to make it more secure. I will be editing it immediately.
Thanks for the config, unfortunately, it did not help at all. I did end up with 503 for no obvious reason  I will dig into it also and post update when I figure it out, but its somewhat releated to websockets, occasionally, I have different log in chrome console about wss: xxx
I will dig into it also and post update when I figure it out, but its somewhat releated to websockets, occasionally, I have different log in chrome console about wss: xxx
I think I did not set up anything there and it was working fine until today’s update for last 2 years or so. I still have http section commented
that’s your problem. See here:
You need to uncomment the http section and it should look like follows:
http:
use_x_forwarded_for: true
trusted_proxies:
- ::1
You need to replace the ::1 with whatever IP your HASS log is saying is being blocked.
A request from a reverse proxy was received from xxx.xxx.xxx.xx, but your HTTP integration is not set-up for reverse proxies
8:18:01 PM – (ERROR) HTTP - message first occurred at 5:59:19 PM and shows up 506 times 
I mean, its pretty obvious  maybe reading release documentation more thoroughly would not harm
maybe reading release documentation more thoroughly would not harm
I know, I had the same moment. 
Aaaand of course it worked. Thanks man!
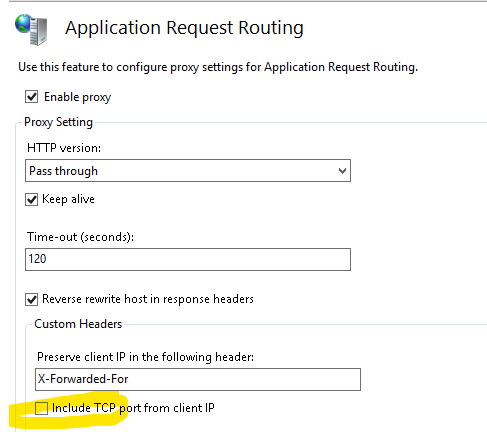
I have the unfortunate situation of being behind an IIS reverse proxy. If any of you find yourself in the same situation you will have to uncheck “Include TCP port from client IP” in the Request Routing Cache–>Server Proxy Settings–>Preserve client IP settings.
HA doesn’t seem to like the header if it has a port. I’m not sure if allowing a port is spec or not. If ports are allowed then this is a bug in HA I guess.
ServerName name.domain.xxx
SSLEngine on
SSLProxyEngine on
SSLProxyVerify none
SSLProxyCheckPeerCN off
SSLProxyCheckPeerName off
SSLProxyCheckPeerExpire off
ProxyPass /api/websocket wss://192.168.0.xx:8123/api/websocket
ProxyPassReverse /api/websocket wss://192.168.0.xx:8123/api/websocket
#https worked, http down <---- resolve
ProxyPass / https://192.168.0.34:xx23/
ProxyPassReverse / https://192.168.0.xx:8123/
Include /etc/letsencrypt/options-ssl-apache.conf
ErrorLog ${APACHE_LOG_DIR}/error.log
CustomLog ${APACHE_LOG_DIR}/access.log combined
SSLCertificateFile /etc/letsencrypt/live/domain.xxx/fullchain.pem
SSLCertificateKeyFile /etc/letsencrypt/live/domain.xxx/privkey.pem
solved by putting https and not http